Table of Contents
Automated Penetration Testing is revolutionizing the way organizations protect their digital infrastructure. As networks become more complex and cyber threats grow increasingly sophisticated, traditional manual penetration testing is no longer sufficient on its own. Manual testing is time-consuming, resource-intensive, and difficult to scale, especially in large enterprise environments. Automated solutions provide a smarter, faster, and more reliable approach by simulating real-world attacks on systems, applications, and networks without constant human intervention. This enables businesses to detect vulnerabilities early, reduce risk, and maintain a robust security posture in an era where a single exploit can have catastrophic consequences.
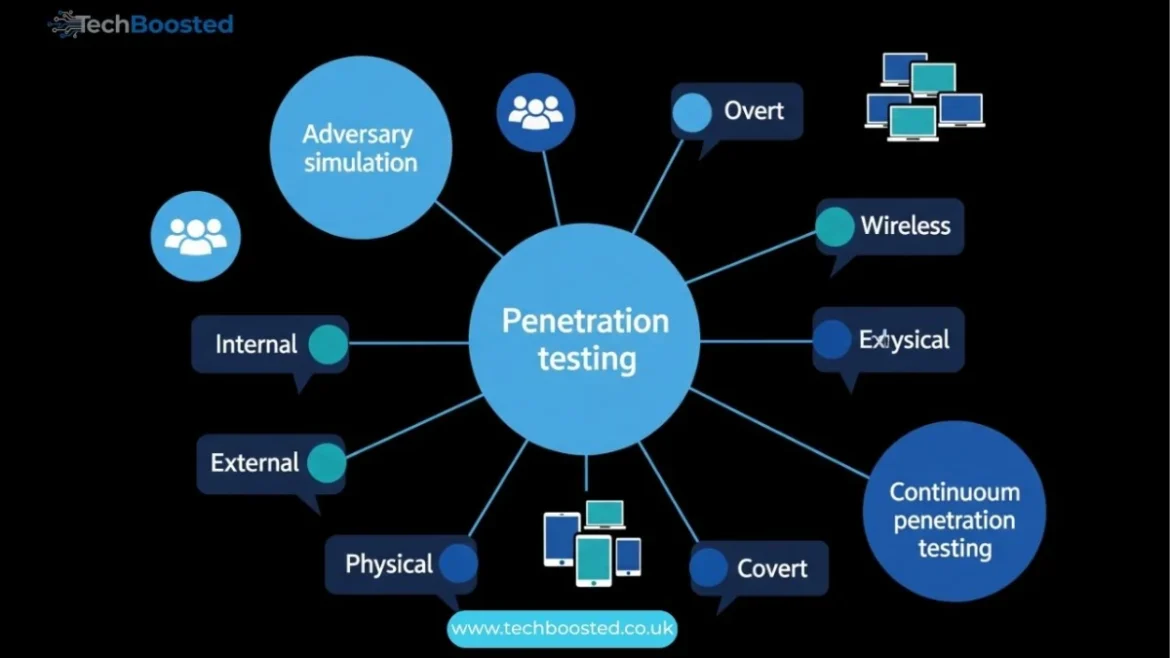
Understanding Automated Penetration Testing
At its core, Automated Penetration Testing uses specialized software to simulate attacks and probe for vulnerabilities in digital environments. These tools perform structured security assessments across networks, web applications, APIs, and cloud infrastructures. Unlike manual testing, which relies heavily on a security expert to discover weaknesses, automated solutions follow pre-defined scripts and vulnerability databases. They can run on a schedule or continuously, providing organizations with real-time insights into potential security risks. This form of testing ensures consistent coverage, repeatable results, and faster identification of weaknesses that may otherwise go unnoticed.
How Automated Penetration Testing Works
The process of Automated Penetration Testing involves several steps designed to mimic the approach of malicious attackers. Initially, the tool maps the network or application environment, identifying open ports, services, and potential entry points. Next, it performs controlled attacks against known vulnerabilities, including outdated software, misconfigurations, weak passwords, and exposed APIs. Each simulated attack is analyzed to determine whether it could compromise security. Results are compiled into detailed reports that categorize risks, prioritize remediation actions, and provide guidance for mitigation. Automation ensures that assessments are comprehensive and repeatable, even in large-scale or dynamic environments.
Key Benefits of Automated Penetration Testing
The benefits of Automated Penetration Testing are substantial. First, it significantly reduces the time and cost associated with manual testing by automating repetitive tasks. It enables organizations to conduct frequent assessments, ensuring that new vulnerabilities are identified quickly. Automated testing also minimizes human error and provides standardized coverage across all assets. In addition, it helps organizations maintain compliance with regulatory frameworks like PCI DSS, ISO 27001, and SOC 2 by delivering documented evidence of consistent security evaluations. Overall, automation improves efficiency, reliability, and proactive defense against emerging threats.
Automated vs Manual Penetration Testing
While Automated Penetration Testing excels at repetitive and large-scale security assessments, manual testing remains essential for complex attack scenarios. Manual penetration testers can uncover subtle business logic flaws, chained exploits, and zero-day vulnerabilities that automated tools might miss. The ideal security strategy combines both approaches. Automated testing provides continuous monitoring and rapid vulnerability detection, while manual testing offers deep insights into complex attack vectors. Together, they create a robust security framework that balances efficiency with expert-driven analysis.
Use Cases for Automated Penetration Testing
Modern organizations employ Automated Penetration Testing in various contexts. DevSecOps teams use it to integrate security early in the software development lifecycle, identifying vulnerabilities before deployment. Cloud-based services rely on automated testing to monitor frequently changing environments. Enterprises use it to maintain security across distributed networks and remote offices. Managed Security Service Providers (MSSPs) deploy automated solutions to assess multiple clients efficiently. These use cases illustrate how automation supports proactive, scalable security in environments where manual testing alone would be impractical.
Limitations of Automated Penetration Testing
Despite its advantages, Automated Penetration Testing has some limitations. Automated tools primarily rely on known vulnerabilities and attack patterns, which means zero-day exploits or highly targeted attacks might go undetected. False positives can occur, necessitating human verification to confirm the severity of issues. Improperly configured tools may lead to incomplete coverage or unnecessary system load. Understanding these limitations is crucial for organizations to integrate automation effectively into a comprehensive security program rather than relying solely on automated testing.
Integrating Automated Penetration Testing in Risk Management
Automated Penetration Testing is a valuable tool for risk management. By continuously identifying vulnerabilities, organizations can assess the likelihood and potential impact of security breaches. Risk management teams can prioritize remediation based on criticality, reducing exposure to high-impact attacks. In addition, automated testing supports compliance reporting, ensuring that organizations meet regulatory and contractual obligations. By providing actionable insights and real-time monitoring, automated penetration testing helps businesses make informed decisions to strengthen cybersecurity defenses.
Choosing the Right Automated Penetration Testing Tool
Selecting the best solution for Automated Penetration Testing depends on organizational requirements, complexity, and security maturity. Key considerations include the tool’s coverage of networks, applications, and cloud environments, ease of integration with existing workflows, quality of reporting, and update frequency. Support for modern architectures, including containerized and microservices-based applications, is essential. Additionally, vendors offering customizable scans, real-time alerts, and integration with SIEM and ticketing systems provide enhanced value. Choosing the right tool ensures that automation improves efficiency without overburdening security teams.
Future of Automated Penetration Testing
The future of Automated Penetration Testing is closely linked to advances in artificial intelligence (AI) and machine learning. AI-driven solutions can adaptively prioritize vulnerabilities based on real-world exploitability and business impact, making automated testing even more effective. As threats continue to evolve, organizations will increasingly rely on automated tools to provide continuous assessment and early warning of vulnerabilities. Automation is expected to become a standard component of proactive security strategies, allowing businesses to stay ahead of attackers and reduce the likelihood of costly breaches.
Best Practices for Effective Automated Penetration Testing
To maximize the value of Automated Penetration Testing, organizations should follow best practices. Conduct regular testing, ideally integrated into DevSecOps pipelines. Validate automated findings with manual checks to reduce false positives. Update vulnerability databases frequently to capture emerging threats. Use comprehensive reporting to prioritize remediation efforts effectively. Train security teams on tool usage and interpretation of results. By following these practices, businesses can ensure that automated testing enhances security while complementing human expertise.
Conclusion
Automated Penetration Testing is a smarter, scalable solution for modern network security. By simulating real-world attacks, organizations can continuously monitor vulnerabilities, reduce risk, and maintain regulatory compliance. While automation cannot fully replace manual testing, it streamlines repetitive tasks, improves coverage, and accelerates remediation. Integrated into a comprehensive security strategy, automated penetration testing empowers organizations to respond proactively to evolving cyber threats, safeguard sensitive data, and optimize the overall security posture of their digital infrastructure.
Frequently Asked Questions (FAQs)
What is Automated Penetration Testing?
Automated Penetration Testing uses software tools to simulate attacks and identify vulnerabilities in systems and networks without constant human intervention.
How does Automated Penetration Testing differ from manual testing?
Automated testing excels at large-scale, repeatable assessments, while manual testing uncovers complex logic flaws and zero-day vulnerabilities.
Can Automated Penetration Testing detect all vulnerabilities?
No, it primarily detects known vulnerabilities. Some complex or zero-day attacks may require manual testing to identify.
Is Automated Penetration Testing suitable for cloud environments?
Yes, automated tools are ideal for dynamic cloud infrastructures where assets frequently change and continuous monitoring is required.
How often should automated penetration tests be run?
Regularly, ideally integrated into CI/CD pipelines for continuous assessment and monitoring of evolving environments.
Does Automated Penetration Testing support compliance?
Yes, it provides documented evidence of security testing, helping organizations meet standards like ISO 27001, PCI DSS, and SOC 2.
Stay connected with Techboosted.co.uk through our comprehensive cybersecurity insights and automated