Table of Contents
In today’s highly connected world, securing the edge has become critical for businesses leveraging IoT networks. Edge devices from industrial sensors to smart home gadgets process vast amounts of data outside traditional IT perimeters, making them vulnerable to attacks. Implementing robust visibility and security solutions ensures organizations can monitor, protect, and manage these endpoints efficiently. By focusing on securing the edge, companies can prevent cyberattacks, maintain operational continuity, and comply with regulations. This article explores the most effective strategies for while optimizing IoT network performance in modern, high-demand environments.
Why Securing the Edge Is a Priority
Securing the edge is essential because IoT devices operate in diverse and often remote environments. Weak authentication, outdated firmware, and unencrypted communications increase the risk of breaches. Visibility and monitoring tools are crucial for identifying anomalies, detecting unauthorized devices, and responding to threats. Enterprises adopting securing the edge strategies can proactively safeguard data while maintaining business continuity. Real-time insights into device activity help IT teams enforce policies, ensure compliance, and prevent downtime, especially in sectors like healthcare, manufacturing, and smart cities.
The Role of Edge Computing in IoT Security
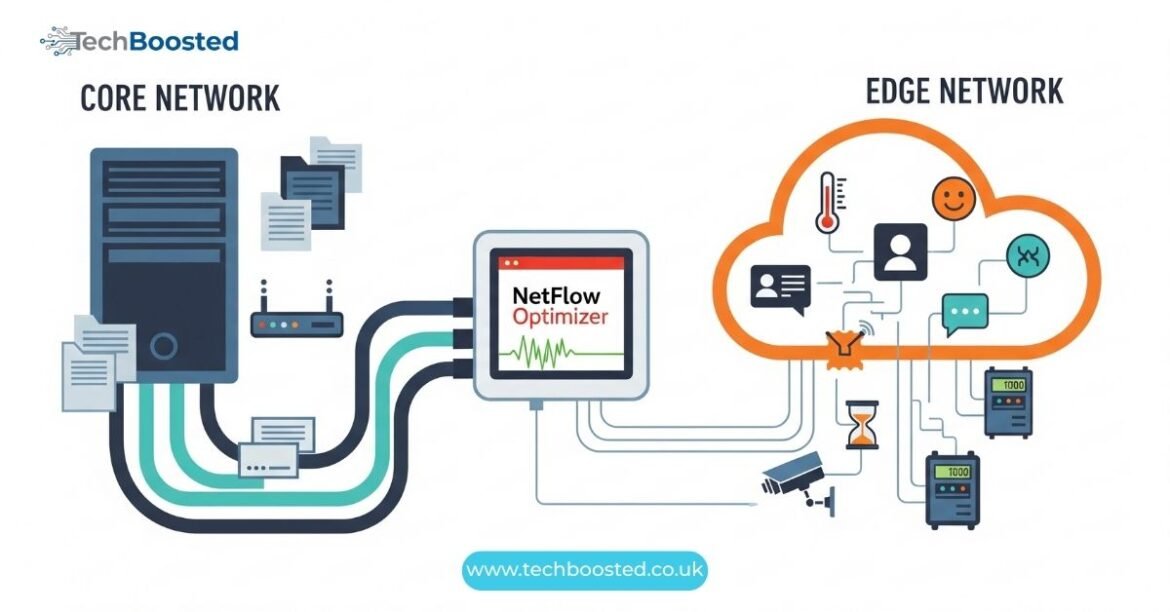
Edge computing enhances performance by processing data closer to where it is generated. However, it also increases the potential attack surface. Securing the edge requires solutions that protect these endpoints while maintaining low latency and high efficiency. Tools such as distributed firewalls, intrusion prevention systems, and AI-based threat detection are integral for securing the edge. By combining edge computing with advanced monitoring, organizations can ensure devices are both fast and secure, achieving the dual goals of operational efficiency and comprehensive protection across IoT networks.
Key Visibility Solutions for Securing the Edge
Effective visibility is the cornerstone of securing the edge. Monitoring tools like network traffic analyzers, behavior detection systems, and asset discovery platforms provide detailed insights into device activity. With these solutions, organizations can identify unauthorized access, monitor communication patterns, and detect anomalies in real-time. Incorporating securing the edge strategies ensures devices remain compliant with security policies and industry regulations. AI-driven analytics further improve the ability to respond to emerging threats, making visibility solutions an essential component of any modern IoT security framework.
Threat Detection and Response

Modern IoT networks face numerous threats, including ransomware, botnets, and insider attacks. Securing the edge requires advanced detection systems that continuously analyze network and device behavior. When suspicious activity is detected, automated responses isolate affected endpoints and alert security teams. Integrating AI with securing the edge practices enables predictive threat detection, reducing the risk of operational disruptions. By combining real-time analytics, automated responses, and policy enforcement, organizations can maintain resilient IoT environments that withstand both known and emerging cyber threats.
Identity and Access Management for IoT
Effective identity and access management (IAM) is key to securing the edge. Controlling who or what can access IoT endpoints prevents unauthorized usage and potential breaches. Role-based access, strong authentication, and regular credential updates are fundamental components of strategies. By ensuring each device has appropriate permissions and monitoring user access continuously, organizations minimize vulnerabilities and enhance the overall security posture of their IoT networks. IAM also supports compliance and audit requirements, critical for regulated industries.
Encryption and Data Protection
Encryption is vital for securing the edge because IoT devices transmit sensitive data across multiple networks. Encrypting data in transit and at rest ensures integrity and confidentiality. Secure protocols such as TLS, along with strong key management, form the backbone of securing the edge practices. Organizations should also implement endpoint encryption and data masking to protect sensitive information. By integrating encryption into their IoT strategy, businesses reduce risk exposure and build trust with customers, regulators, and stakeholders.
Integrating AI and Machine Learning
AI and machine learning play a major role in securing the edge by detecting unusual behavior patterns and predicting potential vulnerabilities. Machine learning algorithms analyze device activity, flag anomalies, and recommend corrective actions in real-time. Leveraging AI within frameworks enables organizations to scale monitoring efforts across thousands of endpoints without adding excessive manual oversight. This approach ensures high performance and security, even in highly complex IoT networks where traditional monitoring tools would struggle to keep pace.
Best Practices for Securing the Edge
Implementing securing the edge strategies requires a structured approach. Key best practices include continuous asset discovery, network segmentation, automated patch management, and frequent security audits. Security must be integrated during device design, including secure boot, firmware updates, and strong authentication. Staff training on IoT risks, combined with real-time monitoring and AI analytics, ensures threats are identified and mitigated promptly. These practices collectively strengthen enterprise IoT defenses while supporting scalability and operational efficiency.
Future of IoT Network Security
The future of securing the edge is closely tied to emerging technologies like zero-trust architecture, blockchain authentication, and federated AI models. IoT networks will continue to expand, and organizations that adopt robust securing the edge solutions now will be better prepared for future threats. Scalable, adaptive security strategies will help maintain operational efficiency, protect critical data, and support regulatory compliance across increasingly complex IoT ecosystems.
What This Means for Enterprise Operations
Securing the edge directly impacts operational efficiency and decision-making. IoT devices generate vast amounts of real-time data that organizations rely on for predictive maintenance, inventory management, energy optimization, and smart city operations. Without proper edge security, sensitive operational data can be intercepted, modified, or blocked, leading to downtime or financial loss. By implementing robust solutions, enterprises gain visibility into device performance, network traffic, and potential vulnerabilities. This ensures business continuity and allows teams to make informed decisions confidently, knowing that data integrity is maintained across the entire IoT ecosystem.
Challenges in Implementing Securing the Edge
Despite its importance, securing the edge is not without challenges. The diversity of IoT devices, from sensors to industrial robots, creates compatibility and management complexities. Many devices have limited processing power, making advanced security software difficult to deploy directly on endpoints. Network latency and bandwidth constraints can hinder real-time monitoring and threat detection. Additionally, rapidly evolving cyber threats require constant updates to security protocols. Organizations must balance operational efficiency with protection by integrating scalable securing the edge strategies, combining cloud management, AI-driven analytics, and adaptive security frameworks to maintain resilience without sacrificing performance.
Conclusion
Securing the edge is no longer optional it is fundamental for modern IoT networks. By combining visibility, threat detection, identity management, encryption, and AI-driven monitoring, organizations can protect devices and data while maintaining operational efficiency. Edge computing enhances performance, but it also increases the need for comprehensive security measures. Implementing holistic strategies ensures businesses remain resilient, compliant, and capable of leveraging the full potential of their IoT ecosystems in the years ahead.
FAQs
What does “securing the edge” mean?
It refers to protecting IoT devices and data at the network’s edge from cyber threats.
Why is securing the edge important for IoT networks?
Edge devices often operate outside traditional IT security, making them vulnerable.
How does AI help in securing the edge?
AI detects anomalies, predicts threats, and recommends automated responses in real-time.
What role does encryption play in securing the edge?
It protects sensitive data both in transit and at rest, maintaining integrity and confidentiality.
What are common strategies for securing the edge?
Visibility tools, IAM, automated patching, network segmentation, and AI monitoring.
How does edge computing affect security strategies?
It increases efficiency but expands the attack surface, requiring targeted security measures.
Stay connected with Techboosted.co.uk through our [IoT network security insights].